What is OCSP Stapling?
OCSP stapling uses the Online Certificate Status Protocol (OCSP) to remove a browser’s need to check with a third party when determining if a security certificate is valid.
OCSP stapling essentially “staples” the status verification to the responding webserver, which you control, rather than relying on a third-party server that you do not.
What is OCSP ?
It is a method used by browsers to make sure a security certificate is valid.
Web browsers check the status of security certificates with third-party vendors. If the certificate is valid, the connection to HTTPS will continue. Learn more about OCSP here.
Web Browsers are using OCSP now
OCSP was used in some form to view the page you are reading now. So OCSP is used now, but whether or not OCSP Stapling is used depends on how an individual web server is configured.
OCSP: Web browsers have decided to use this for you (you the webmaster have no say in this)
OCSP Stapling: You, the webmaster, can decide to use (you have control of whether you use this or not)
In a nutshell
OCSP is an effective way to check if key certficates are valid, but it presents some significant issues as well. Currently, the way OCSP is implemented by browsers raises three major concerns: privacy, performance, and a potential point of failure.
OCSP is being used now, and OCSP Stapling is an improved method of OCSP that you can decide to use.
OCSP (without stapling) Issues
One step of OCSP involves checking the validity of your security certificate with a third-party server.
It is important to note that you as a webmaster have no control over the way browsers implement this step unless you use stapling.
If you are not currently using OCSP stapling you will experience three issues:
Privacy:
When a browser is checking the status of a certificate by querying a OCSP server, it can potentially affect the privacy of a user by collecting the requests and determining where, when, and by who they were made.
Performance:
OCSP adds an additional request to the process of serving a webpage. This additional request makes a user wait longer to see your webpage. Depending on the speed of the OCSP server, that additional time may be a significant issue.
Potential Point of Failure:
As explained above, the OCSP system browsers use adds an additional step of querying an OCSP server. This means that there is now a third party involved that you as a webmaster have no control over. So if the OCSP server is failing, this can have negative consequences, for both you and your users, even if your server is up and running perfectly.
These issues can be resolved with OCSP stapling, but it must be implemented on your server to reap the rewards.
What OCSP Stapling does
Let’s explore the difference between two connections, one made with OCSP and one made with OCSP stapling.
In a normal OCSP connection without stapling (the way browsers are doing it right now)
There are basically three steps to validate a security certificate, involving your server, the web browser, and a third-party OCSP server.
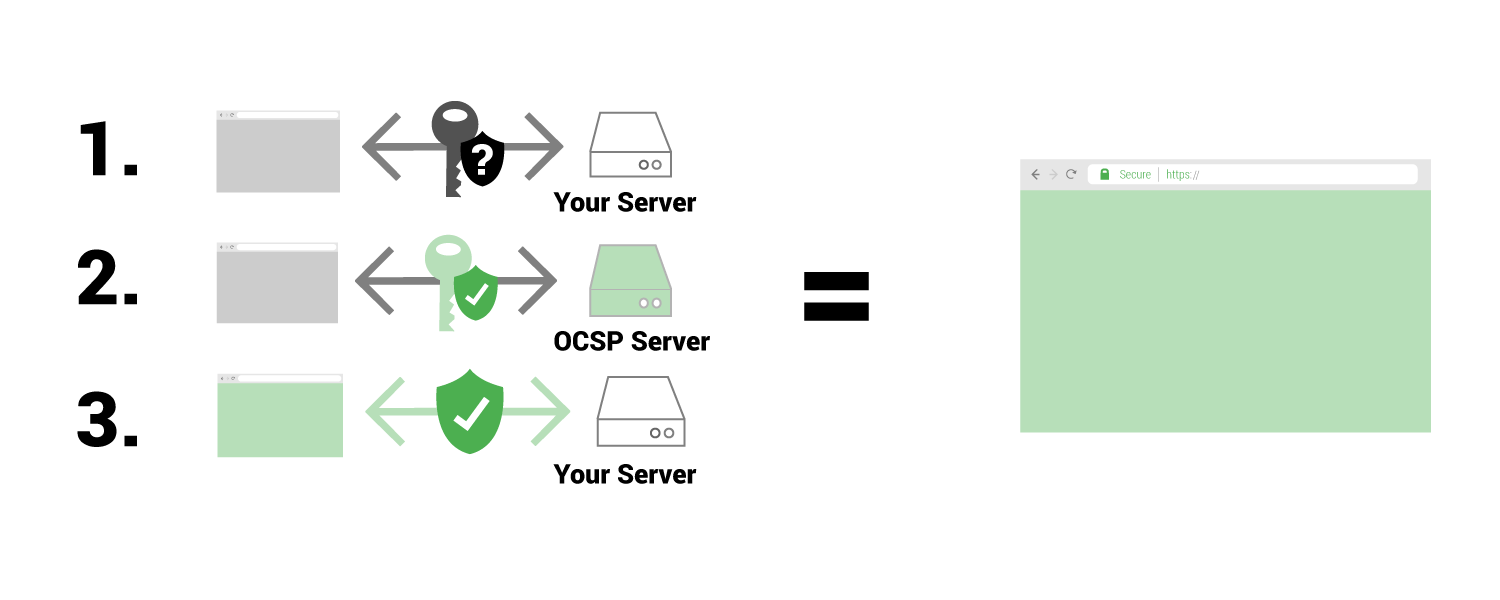
When you add the user into the equation it looks something like this…
- A browser will get a request from a user to visit example.com
- The browser requests the page from example.com
- Browser receives a response from example.com indicating it is a secure page
- Browser then will contact a OCSP server to see if example.com’s certificate is valid
- Once the browser verifies the certificate is valid, it will show the user the page
In a OCSP connection with stapling
There are basically two steps to validate a security certificate, which only requires the web browser and your web server (no third party required).
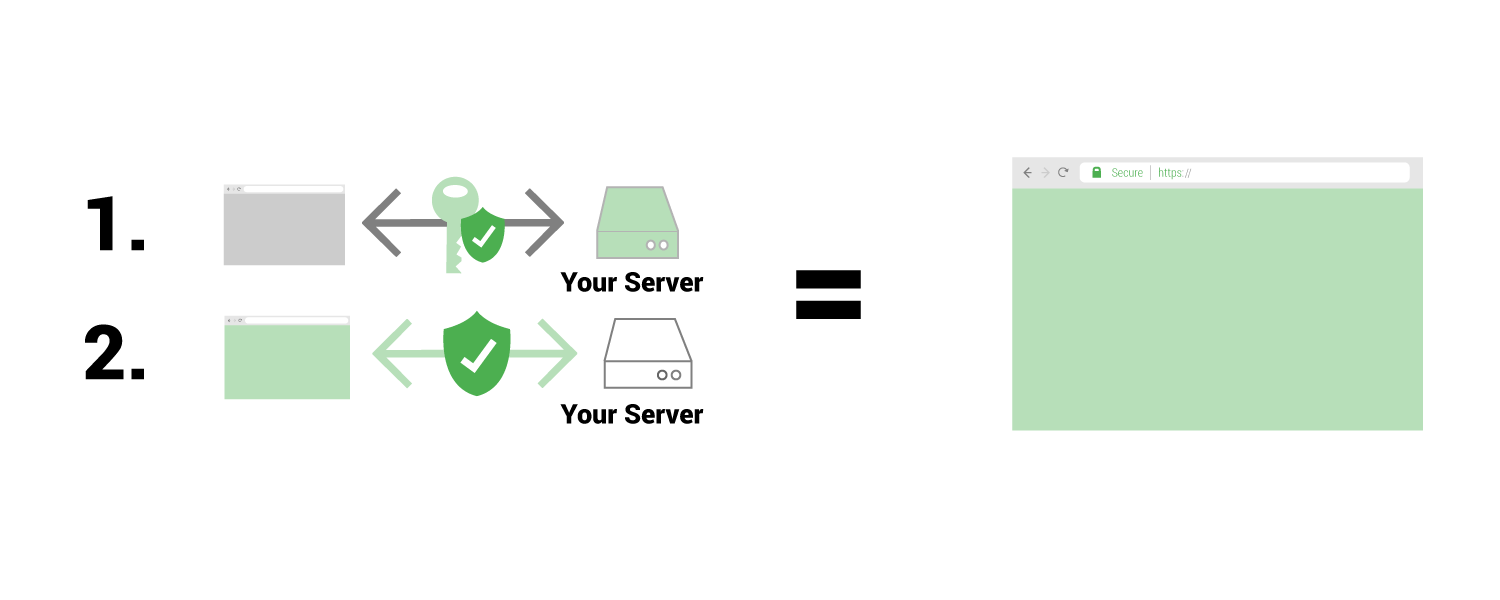
With the user in the equation it looks something like this…
- A browser will get a request from a user to visit example.com
- The browser requests the page from example.com
- Browser receives a response from example.com indicating it is a secure page with a valid certificate and shows the page to the user
Advantages of OCSP stapling
When a server is properly configured to use OCSP there are…
Performance gains – one less server to deal with
Privacy gains – no third parties involved in your traffic
Fewer points of possible failure – With fewer things involved in serving your pages, there is less that can go wrong
Control Issues
It is beneficial to implement OCSP stapling even if only to gain more control over your traffic.
I do not want to depend on third party servers that I do not control. Nobody does, yet that is exactly what is occurring if you are not using OCSP stapling. You are handing some control over to third parties that you may or may not be able to rely on.
See more of our HTTPS articles
 Table of Contents
Table of Contents